WIFI
WIFI¶
802.11is a common standard for wireless LANs today.
Common authentication methods:
- None
WEPWPA/WPA2-PSK(pre-shared key)WPA2 802.1X(radiuscertificate)
WPA-PSK¶
The general process of authentication is shown:
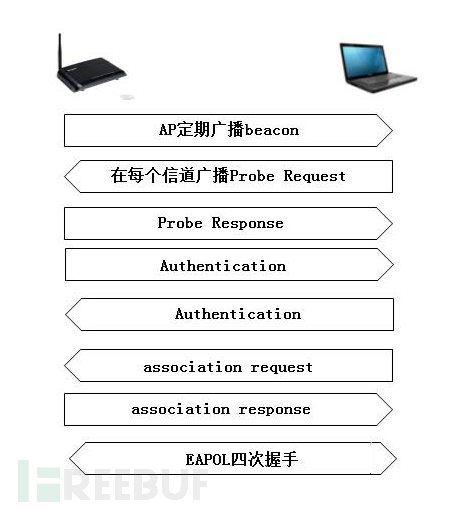
Four handshakes:
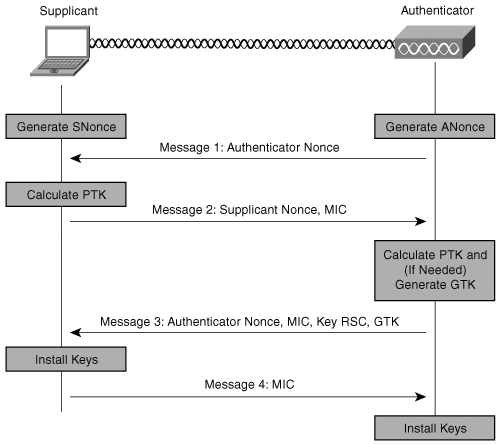
- 4 Ways handshake starts at the AP, it then generates a random string (ANonce) and sends it to the requester.
- The requester also generates its own random SNonce, and then uses these two Nonces and PMK to generate the PTK. The requester replies message 2 to the authenticator and a MIC (message integrity code) as the verification of the PMK.
- The authenticator sends information from the requester’s message 2 back to the requester, once it’s verified, it will generate GTK if needed. Then, sends it as message 3.
- The requester receives message 3, verifies the MIC, installs the key, sends a message 4, and a confirmation message. The verifier receives message 4, verifies the MIC, installs the same key.
CTF Example¶
Experiment Lab - shipin¶
Download the PCAP file here
From a large number of Deauth packets, we obtained the handshake packets in the traffics, which we can use to crack the WIFI password.
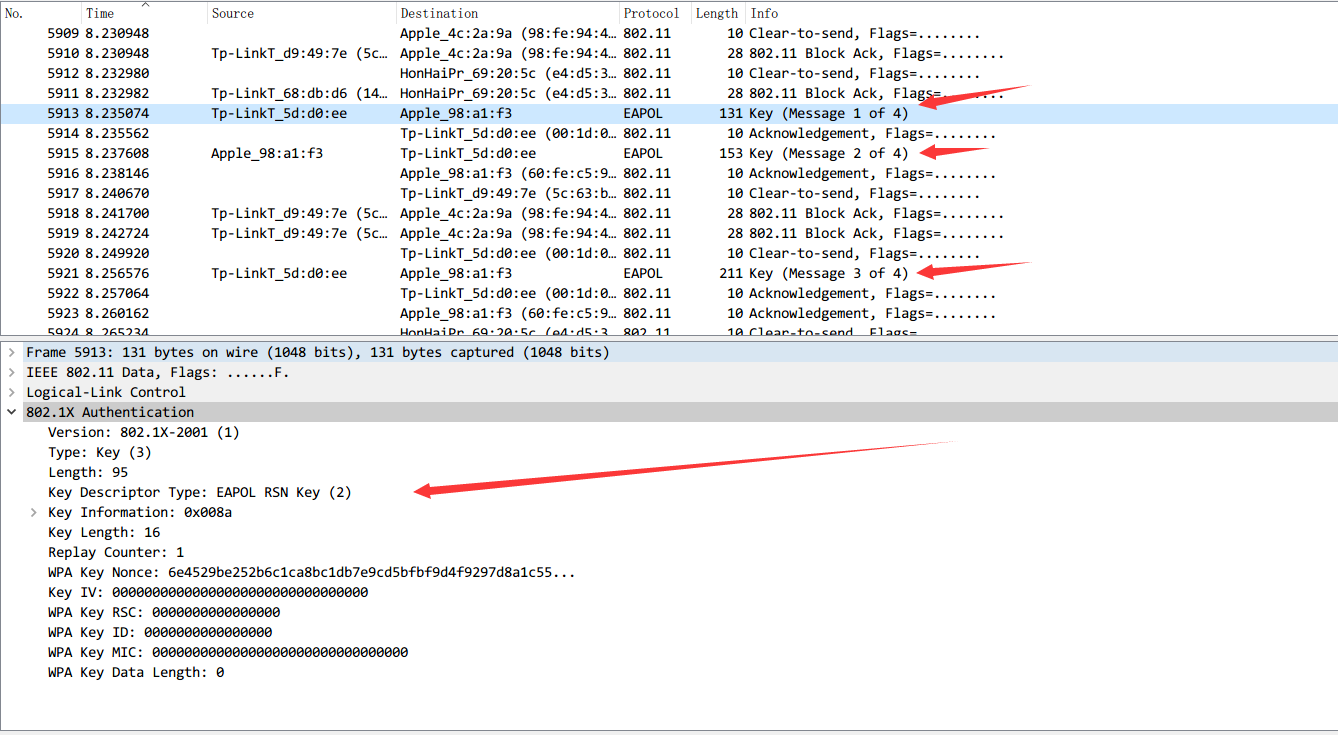
Next, we crack the password.
You can use the aircrack suite.
Run the command aircrack-ng shipin.cap -w /usr/share/wordlists/rockyou.txt
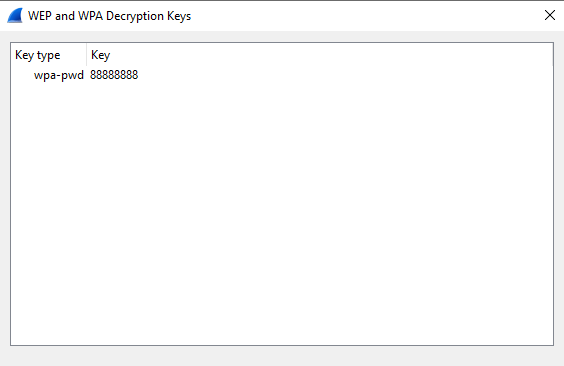
We found the key, 88888888.
Now, we can use the key found to decrypt the packets within the WIFI network.
Go to Edit --> Preferences --> Protocols --> IEEE802.11 --> Edit in Wireshark.
Fill in the form key-type:key to decrypt the packets to see the clear text traffic.
There is no flag in this challenge.
References¶
本页面的全部内容在 CC BY-NC-SA 4.0 协议之条款下提供,附加条款亦可能应用。